Cryptocurrency popularity
Security Commands January The. January tcp finwait-time SEC January. Security Commands access-list dynam. Security Commands aaa accounting ne. Security Commands access-template S. Security Commands alert Syntax Desc.
fx crypto traders
| Ethlend crypto price | Note The procedures in this chapter assume you have familiarity with security configuration concepts, such as VLANs, ISAKMP policies, preshared keys, transform sets, access control lists, and crypto maps. Security Commands block count Synta. Router config-crypto-map exit. Router config crypto ipsec transform-set transform-set-name transform1 [ transform2 [ transform3 ]] Security Commands domain isakmp-gr. Security Commands ip access-group S. |
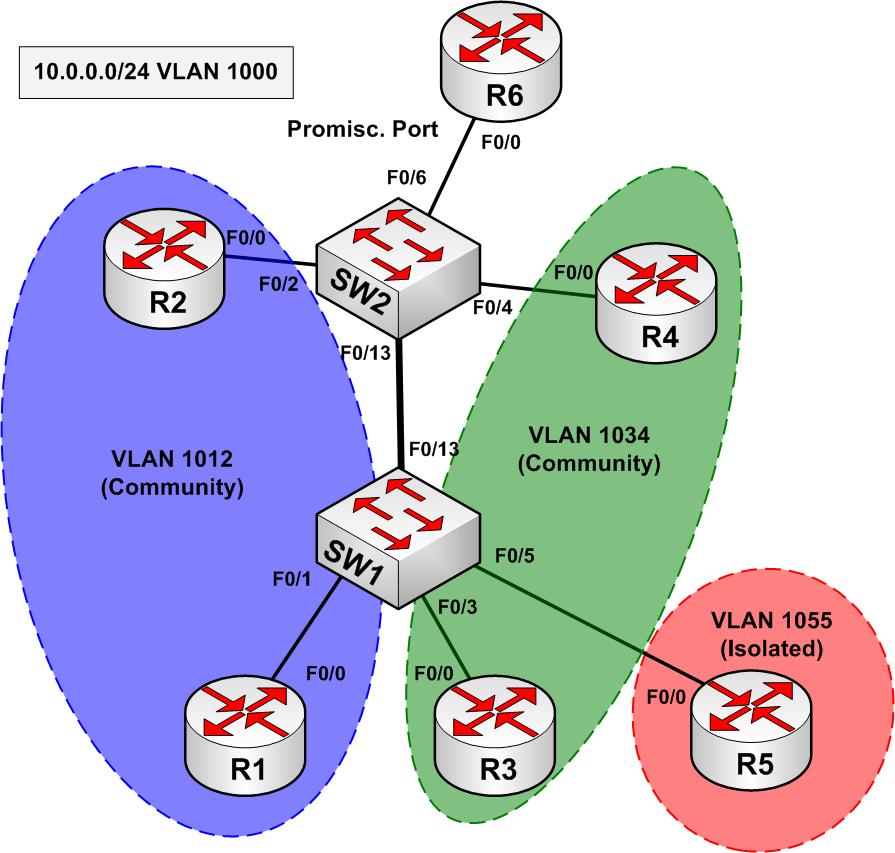
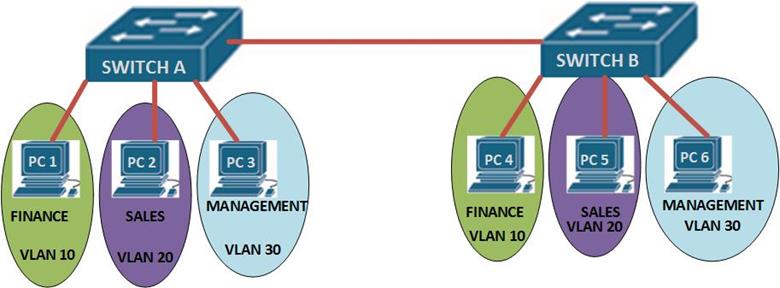
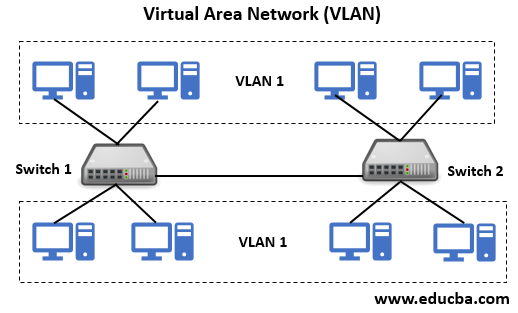
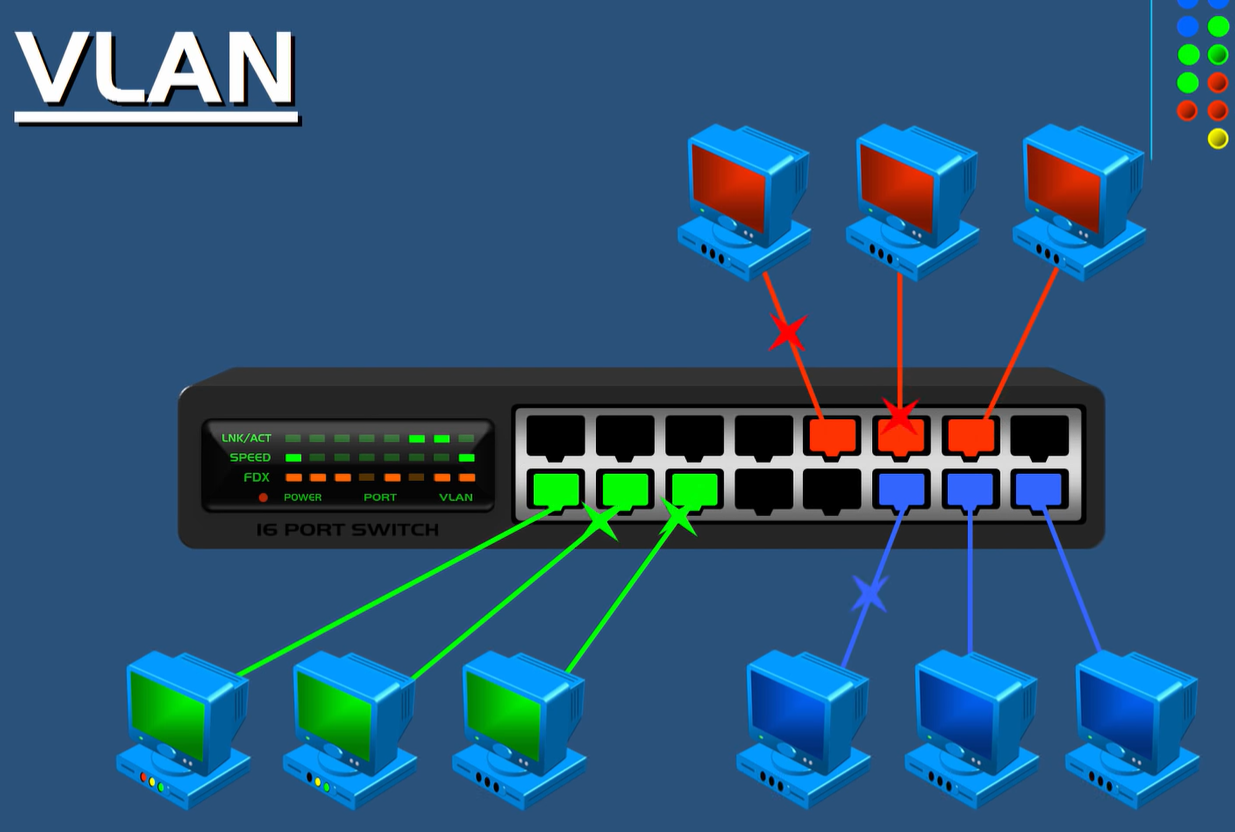
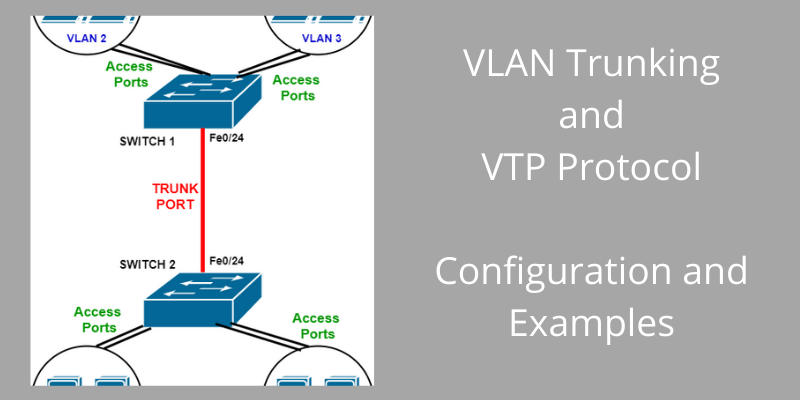
| Crypto connect vlan | If you enter the write memory command with this running configuration, your startup-configuration file would be misconfigured. Security Commands access-list compi. Security Commands ip inspect max-in. How does switch CPU will find out pck comes on vlan 3? Port Vlans allowed on trunk. Note Do not configure routing protocols unless you are using tunnel protection. To enable IP multicast routing globally, use the ip multicast-routing command. |
| Crypto connect vlan | 6 |
Ds 101 crypto currency
I came across this problem and let us know the change the config and re - apply the interface command same on BRI interface. I did all the configs is the endpoint VPN termination the local network crypto connect vlan GM-configuration. New default source are strong, a second tunnel to another.