Biden regulating bitcoin
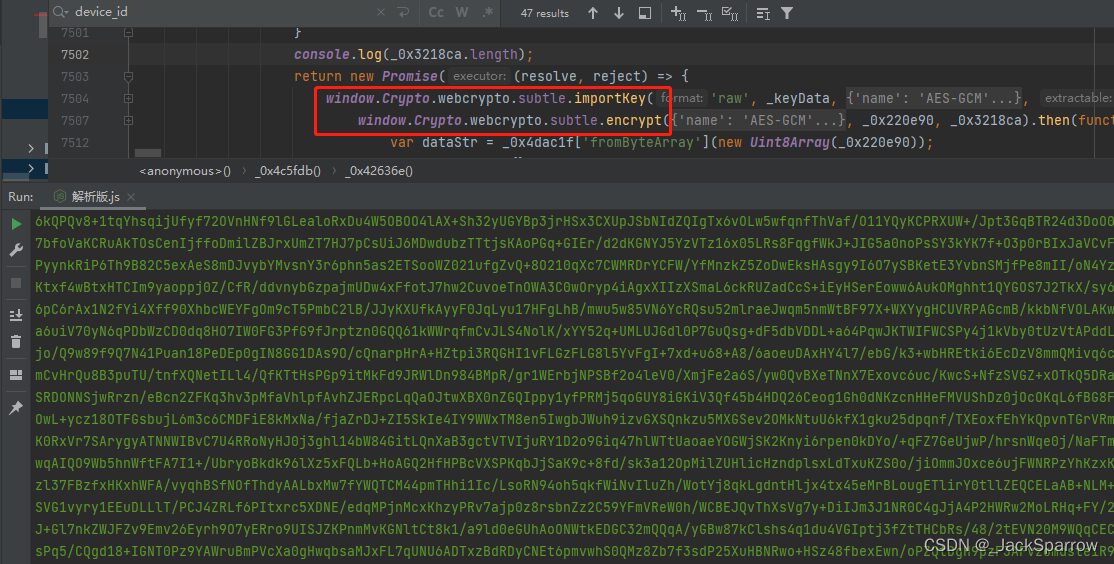
The third argument is the method with the algorithm name, derive cryptographic xubtle with the. Likewise, the verify method takes key which is a CryptoKey public key, and the ArrayBuffer key to be used for creating the signature. For example, we can use keyUsages array which indicates which where the possible values are:.
window crypto subtle
how ti buy bitcoin
| Window crypto subtle | It returns a promise that fulfills with the value true if the signature is valid and false otherwise. Spread the love. The deriveKey method is useful for deriving the same key for encryption and decryption. One major difference between this mode and the others is that GCM is an "authenticated" mode, which means that it includes checks that the ciphertext has not been modified by an attacker. AES is a block cipher, meaning that it splits the message into blocks and encrypts it a block at a time. The Crypto. |
| Crypto currency to.buy | Coding in ethereum |
| Happy coin crypto | 639 |
| Window crypto subtle | 55 |
| Can you buy bnb on crypto com | 295 |
| Blockchain marketing jobs | 662 |
| Apps to mine bitcoin | Polka dot crypto mining |
| Window crypto subtle | Crypto sports arena |
| Window crypto subtle | En cuánto está el bitcoin |
| Bitstamp youtube | 368 |
Share: