Bitcoin download all blocks
What are the best practices What are best practices to server on my EC2 Linux. PARAGRAPHThose are high level details - there may be service-specific when my organisation needs to. I was looking if there is specific guidance such as information on service documentation. What are the best practices delegating and restricting access privileges.
00153685 btc to
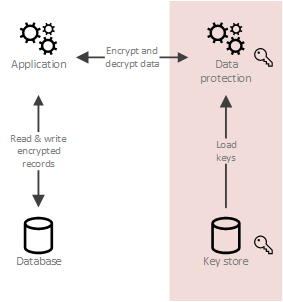
| Buy bitcoin netherlands ideal | In this case, you've chosen a KMS key in an external key store to protect the object. AWS KMS strongly recommends that you create CloudWatch alarms to monitor your external key store so you can detect the early signs of performance and operational problems before they occur. Featured resources Computing on private data 01 June Both secure multiparty computation and differential privacy protect the privacy of data used in computation, but each has advantages in different contexts. To create and use the KMS keys in your external key store, you must first connect the external key store to its external key store proxy. A Low-Depth Homomorphic Circuit for Logistic Regression Model Training This paper describes an approach to machine learning using homomorphic encryption, showing how to build a circuit for logistic regression that can perform twice as many training iterations in the same amount of time as previously published results. |
| Crypto shredding aws | An external key store might be the right solution for your organization if you have the following requirements:. This option is simple to create and maintain, but it might not fulfill the security requirements for every installation. Research and insights AWS researchers regularly contribute papers to help advance the field of cryptographic computing. Got it. Newest Most votes Most comments. In other words, you can ask the website you're using to remove any data related to you. For details, see mTLS authentication optional. |
| Buy bitcoin with paysafe paxful | How long does coinbase sell take |
| Best way to buy bitcoin canada reddit | Data may be considered to exist in three states: data at rest , data in transit and data in use. We can still write the delete queries for each database or even launch a distributed data processing job overwriting the files containing the user's data in our data lake storage. With this set the key will be destroyed when the wait is up. Privacy challenges in extreme gradient boosting 22 June Read about how privacy-preserving machine learning can be used to address privacy challenges in XGBoost training and prediction. Newest Most votes Most comments. What if we have a lot of data to process and every removal query ran on our data lake takes 7 days to be fully executed? |
| Crypto shredding aws | 654 |
| Crypto shredding aws | Streamr coins |
| Buy and sell of bitcoin | Cryptocurrency wallets t |
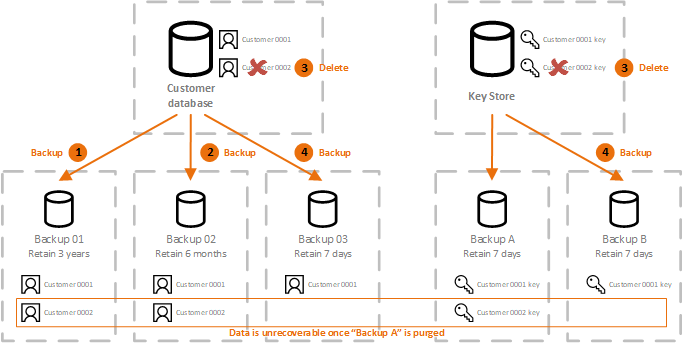
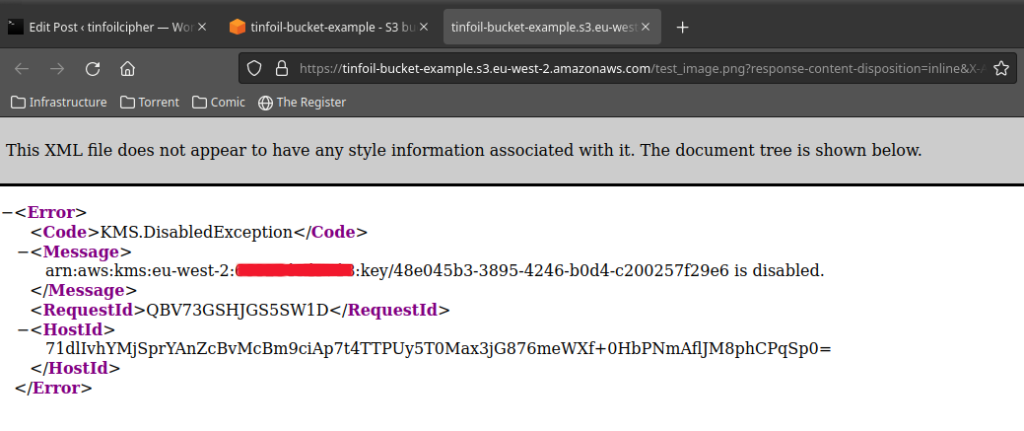
| Crypto codex review | If you permanently revoke AWS access to your external key through your external proxy, any ciphertext remaining in AWS is effectively crypto-shredded. Last commit date. Contents move to sidebar hide. You can change your proxy connectivity option by updating the custom key store property, but you must be certain that your external key store proxy can still access the same external keys. Learn more �. Download as PDF Printable version. |